August 2017 Security Update Advisory (CVE-2017-12939)
Vulnerability Details
CVE ID: CVE-2017-12939
Type: Remote Code Execution
Discovered: 2017/08/13
Discovered By: Rio
Patch Availability: 2017/08/18
Affected Operating System: Windows
Affected Versions: All (Windows)
Severity: High
Patch Versions:
- [1] 5.3.8p2 (Win) (Mac)
- [2] 5.4.5p5 (Win) (Mac)
- [3] 5.5.4p3 (Win) (Mac)
- [4] 5.6.3p1 (Win) (Mac)
- [5] 2017.1.0p4 (Win) (Mac)
- [6] 2017.2.0b8 (Win) (Mac)
Please note: The Mac version is provided as a courtesy for team environments using Windows and Mac. The Mac version is NOT affected by the identified vulnerability.
If a patch is not available for your version, please use the Mitigation Tool [7] (All versions).
An input string validation issue was identified in the Unity Editor affecting the Windows platform that could lead to Remote Code Execution (RCE), allowing an attacker to potentially execute code remotely in the user’s computer.
Remediation Steps
Determine the version of your Unity Editor
Open a Unity project.
The Unity version is visible in the main window title.
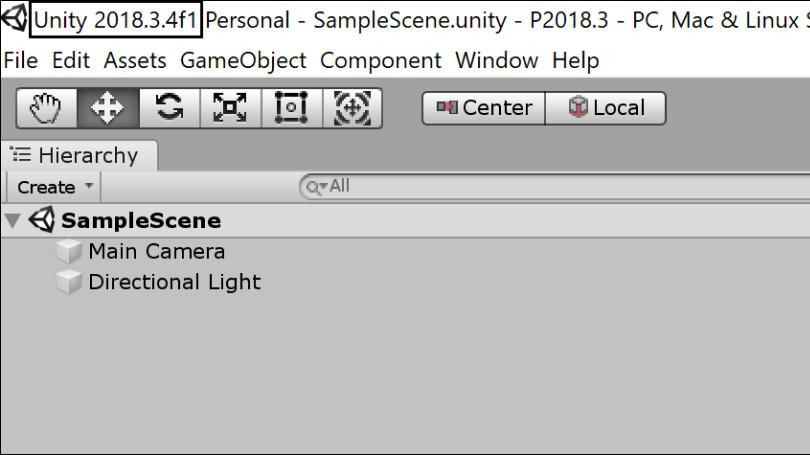
In the File menu choose Help -> About Unity.
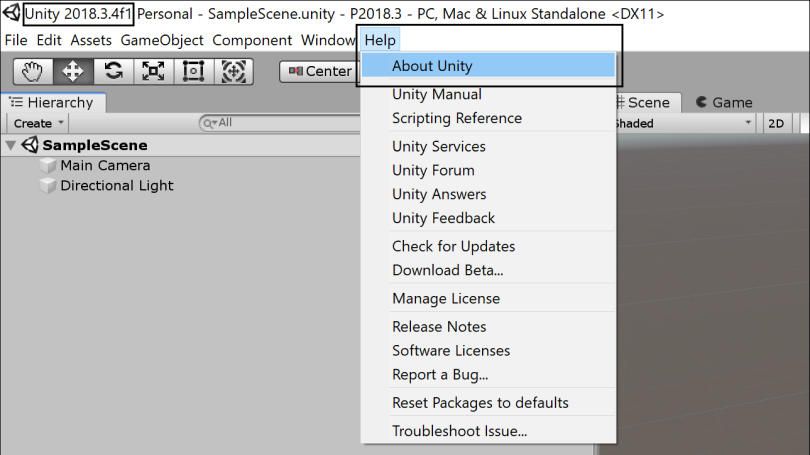
The Unity version is shown in the About Unity window.
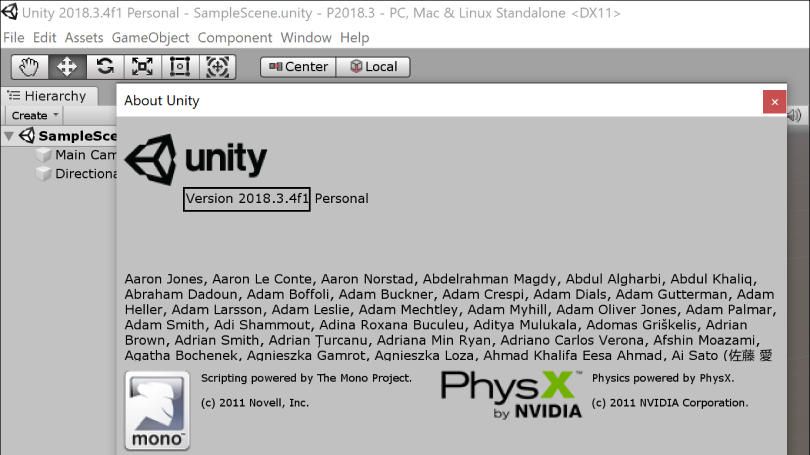
Install Update
If your version of the Unity Editor is not one of the listed in the Patch Versions of the Vulnerabilities Details section above you can continue with the update installation as follows.
To install the update you can use the Unity Editor update checker available in the File menu Help -> Check for Updates.
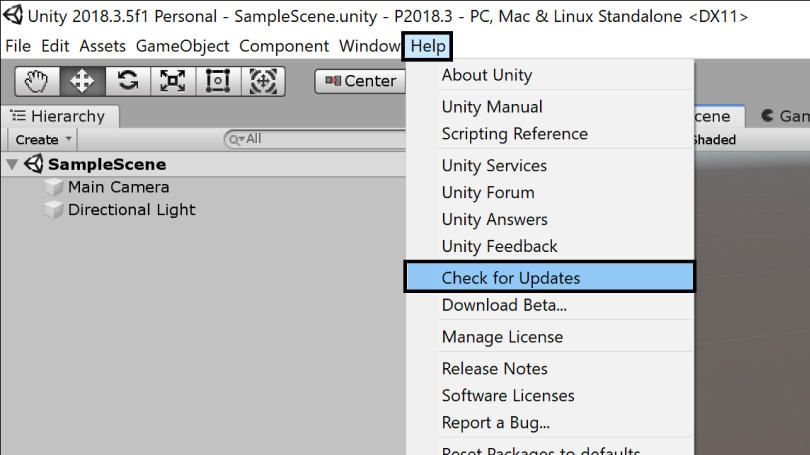
Additionally, you can download and install the corresponding patch for your version of the Unity Editor. The download links are available in the Patch Versions of the Vulnerabilities Details section and in the References section.
Mitigation Tool
If your version of the Unity Editor is not listed, or you are unable to install the update at this time, you can use the Mitigation Tool Guide [7].
Please keep in mind the recommended action is to install a fixed version of the Unity Editor.