May 2020 Security Update Advisory (CVE-2020-12630, CVE-2020-12631)
Vulnerability Details
CVE ID: CVE-2020-12630, CVE-2020-12631
Type: Denial of Service
Discovered: 2020/01/31
Discovered By: Jack Baker
Patch Availability: 2020/05/19
Affected Operating System: All supported platforms
Affected Versions: All
Severity: High
Patch Versions:
- [1] 2019.3.14f1
https://unity3d.com/unity/whats-new/2019.3.14 - [2] 2018.4.23f1
https://unity3d.com/unity/whats-new/2018.4.23 - [3] 2017.4.40f1
https://unity3d.com/unity/whats-new/2017.4.40 - [4] 2020.2.0a11
https://unity3d.com/unity/alpha/2020.2.0a11 - [5] 2020.1.0b9
https://unity3d.com/unity/beta/2020.1.0b9
Two out-of-bounds memory issues were identified in the Unity Multiplayer and Networking UNET feature affecting games and applications built with the Unity Editor using UNET. These issues could lead to Denial Of Service (DoS), allowing an attacker to crash the Unity process, and potentially the game or application.
Remediation Steps
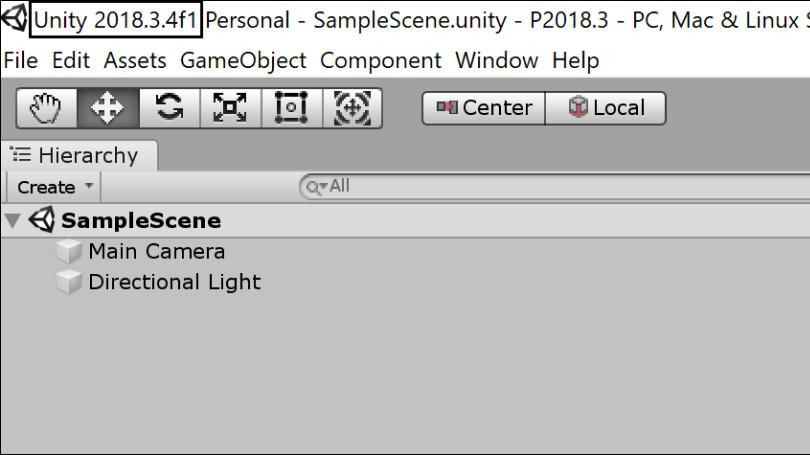
Determine the version of your Unity Editor
Open a Unity project.
The Unity version is visible in the main window title.
Install Update
If your version of the Unity Editor is not one of the listed Patch Versions of the Vulnerability Details section above you can continue with the update installation as follows.
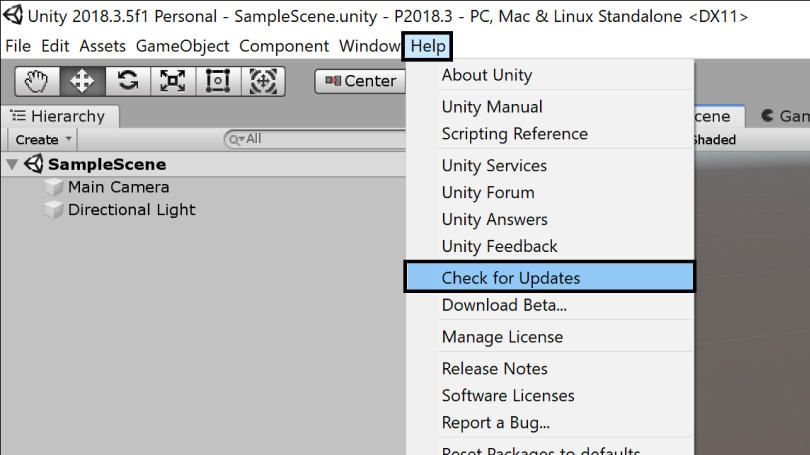
To install the update you can use the Unity Editor update checker available in the File menu Help -> Check for Updates.
Additionally, you can download and install the corresponding patch for your version of the Unity Editor. The download links are available in the Patch Versions of the Vulnerability Details section and in the References section.
Build and deploy
Once you have updated the Unity Editor, you can move forward with making a new build of your game or application and deploy the new fixed version.
FAQ
What type of vulnerabilities were addressed in this update?
+Do these vulnerabilities affect built games/applications in any way?
+What Unity features are affected?
+Will I need to rebuild asset bundles due to the update requirement?
+What platforms are affected?
+What platform versions are affected?
+What versions of Unity are affected?
+What versions of the Unity Editor are being patched?
+Will my specific version be patched?
+What about versions 5.6 and older?
+I have a locked-down older version of Unity 5.x.x. Will you produce a patch for the exact version of Unity that I’m using?
+How do I know if I’ll need to rebuild my asset bundles?
+References
- [1] 2019.3.14f1
https://unity3d.com/unity/whats-new/2019.3.14 - [2] 2018.4.23f1
https://unity3d.com/unity/whats-new/2018.4.23 - [3] 2017.4.40f1
https://unity3d.com/unity/whats-new/2017.4.40 - [4] 2020.2.0a11
https://unity3d.com/unity/alpha/2020.2.0a11 - [5] 2020.1.0b9
https://unity3d.com/unity/beta/2020.1.0b9